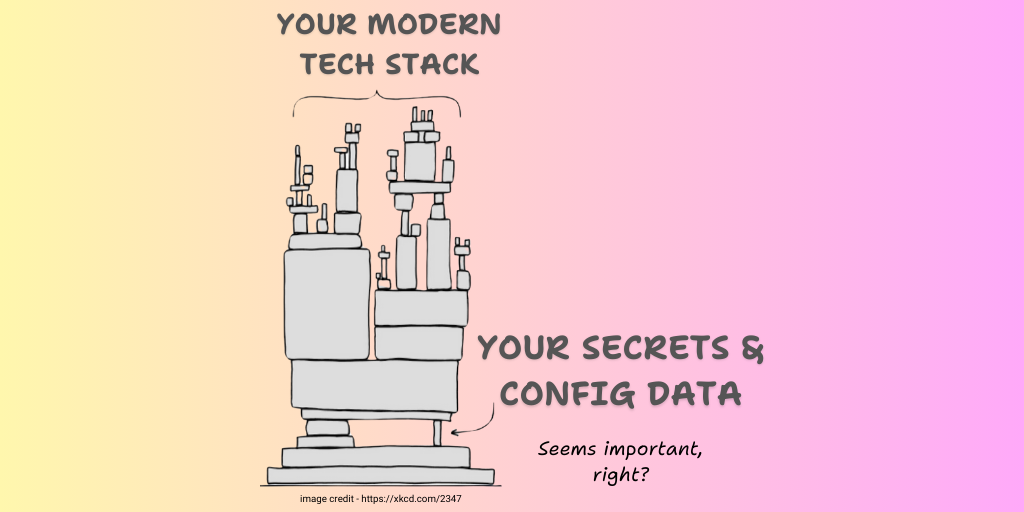
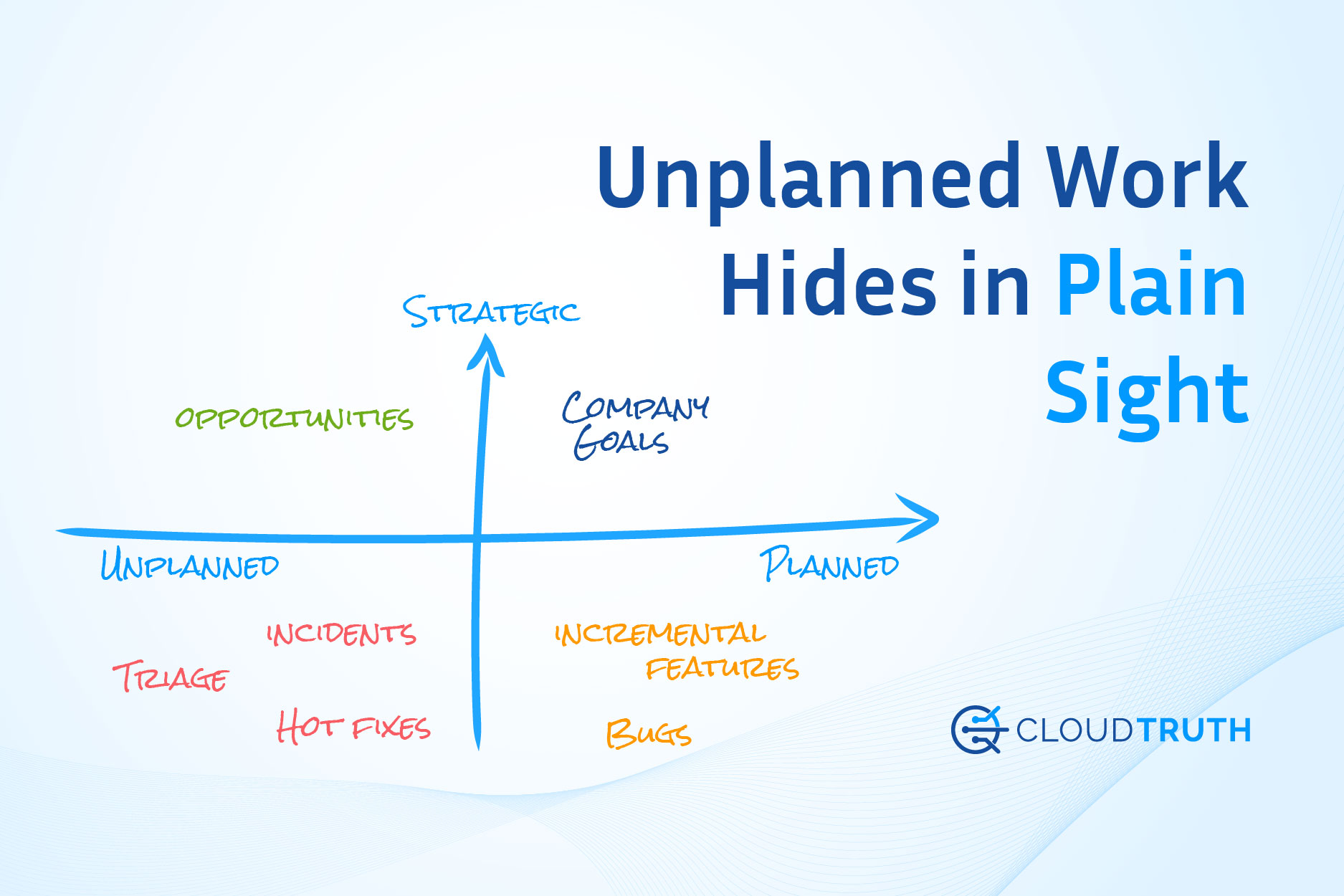
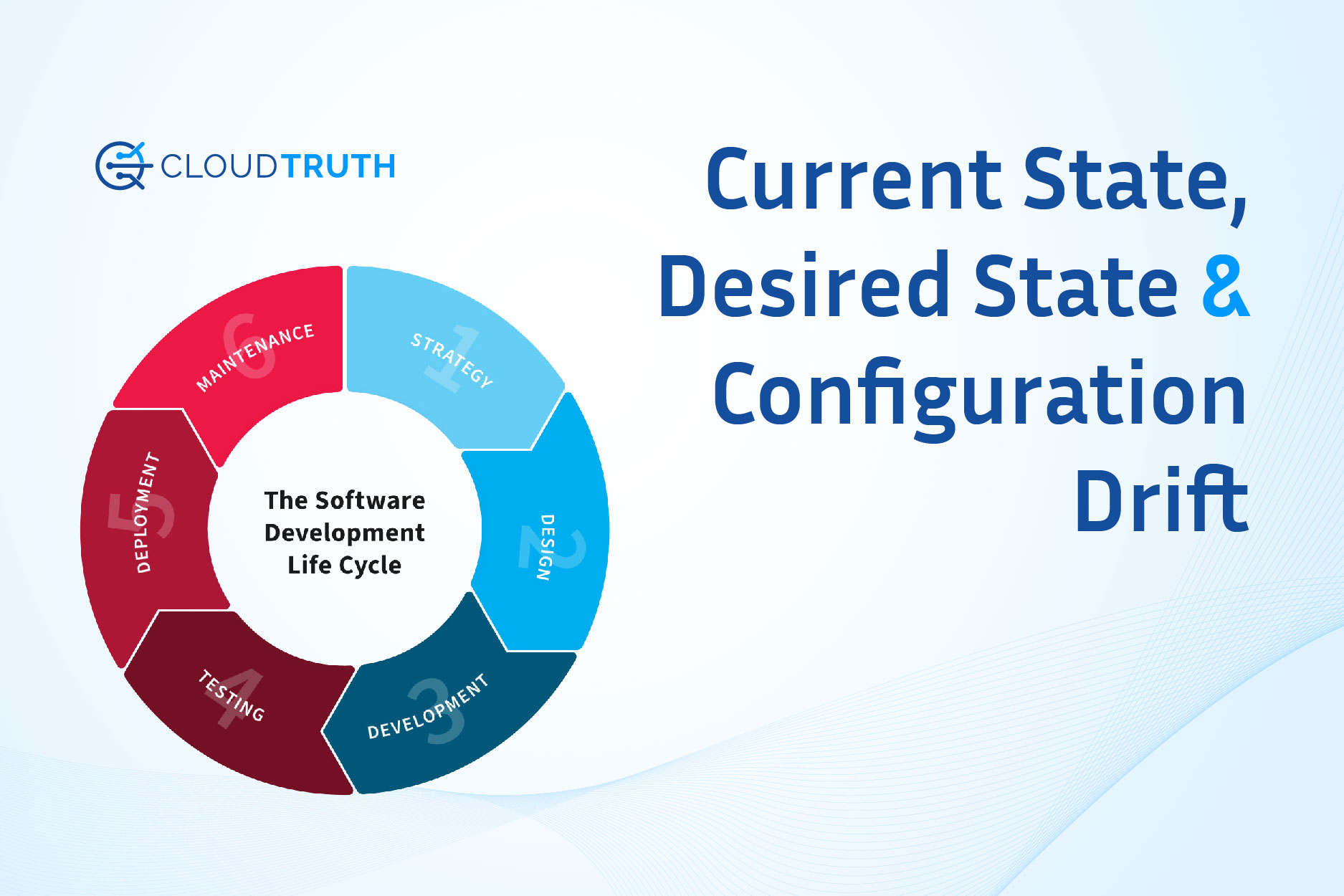
- Platform
- Why Us?
-
- Trusted by leading enterprise engineering teams.
- Enterprise-level support from config, IaC & cloud experts.
- Hosted on your platform or ours.
- Sync your config from anywhere.
- Our Mission
- News
-
- Trusted by leading enterprise engineering teams.
- Enterprise-level support from config, IaC & cloud experts.
- Hosted on your platform or ours.
- Sync your config from anywhere.
-
- Pricing
- Resources
- TruthTalk
TruthTalk
Uncover the secrets to cloud configuration compliance,
stay on top of industry news, & explore our latest findings.